Occasionally, I want to check and see what the kids are up to online. I don’t have a content filter set up yet (it’s on the to-do list) but we run Bind as a local-network domain name server (DNS). To see what someone’s doing, I just use the tail and grep utilities to view Bind’s log files.
Every time someone on the network clicks on a link or types in a URL, that request is routed via the local network DNS. Using tail lets me see current activity in DNS server’s log files. With grep, I filter out irrelevant information to see only the activity of the PC or laptop I’m interested in.
Using tail to check DNS activity from the command line
First, you need to tell Bind to log its activity. Without this, there won’t be anything for you to see. Open the command line and type this:
sudo rndc querylog
Check whether this has worked by typing the following:
sudo rndc status
Bind will spit out a chunk of text in response to this command. Look for the line:
query logging is ON
If it says OFF, then something has gone wrong. Try restarting Bind (sudo service bind9 restart) and then refer to the Bind troubleshooting tips on ubuntu.com.
Once querylogging is enabled, you can easily see current DNS activity by typing:
tail -f /var/log/syslog
The tail utility shows you the last 20 lines of any file, in this case syslog. The -f command stands for follow: telling tail to display new lines as the file grows. Now you just need to sit back and watch what everyone’s up to as they surf the web.
Befuddled by programmatic advertising
And that’s the catch. You’re watching everyone. It’s a little unethical and, even on a small network, impractical. If just one person connects to a major site, it generates dozens of DNS requests in seconds, as your browser pulls together all the dynamic ad-content required to build the page.
And that’s before you factor in activity from your home’s consoles, PCs and mobile devices all paging various cloud services and update servers. On even a moderately busy network, it very quickly becomes almost impossible to separate noise from meaningful data.
Filter out ad-servers with grep
The answer is grep. Grep is a tool that lets you parse a file for a specific word or term and then display only those lines in the file which contain that term. In our case, we want to see lines containing the IP address of the networked device we want to monitor.
Assuming that device in question has the static IP address 192.168.1.31, we type:
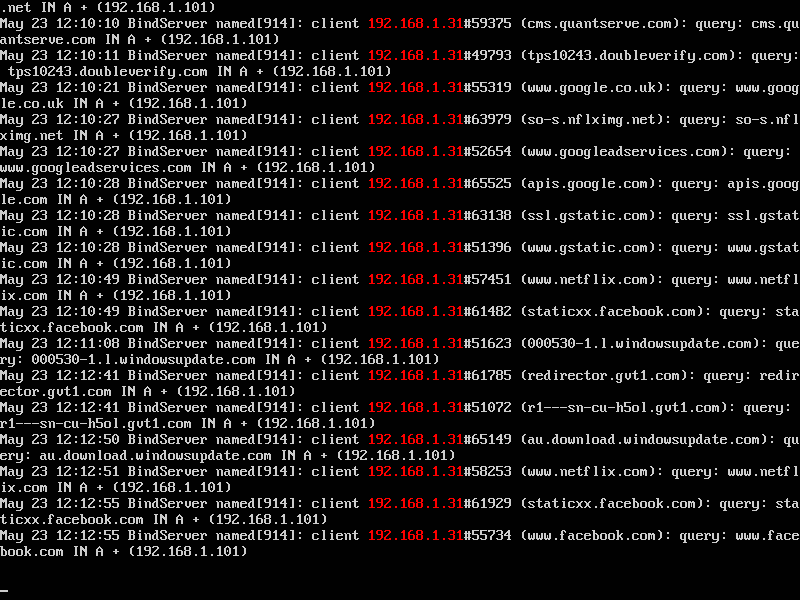
tail -f /var/log/syslog | grep 192.168.1.31
The functions of tail and -f remain unchanged. The command grep 192.168.1.31, tells the system that you only want to see lines containing the IP address 192.168.1.31.
So now you really can sit back and check the network activity of specific devices. In our screenshot, taken on a VMWare machine not the real server, we can see that someone is watching Netflix, checking out Facebook, and has just entered a Google search.
It’s not the most user friendly of systems. At times, it can be hard to filter out significant activity from requests to ad servers. And when someone is surfing a content-rich site such as YouTube, you can tell they’re on the site but not what they’re looking at.
But with a bit of attention, you can build a fairly good picture of what someone’s browsing. You can certainly see if someone’s surfing the web when they should be doing their homework.
Leave a Reply